Managing Risk In Information Systems | Ment's increasing awareness that something had to be done to better. Risk management is nothing new. Information risk management or irm, is a form of risk mitigation through policies, procedures, and technology there are now regulatory requirements, such as the general data protection regulation (gdpr) or apra's cps 234, that mean managing your information systems correctly must be part. Managing risk in information systems 2nd ed. Part of the jones & bartlett learning information systems security & assurance series revised and updated with the latest data in the field, the second edition of managing risk in information systems provides a comprehensive overview of the sscp® risk.
If you don't properly manage it risks, they can also. As explained in chapter 1, security ensures the confidentiality, integrity, and availability of information assets. Jennifer bridges, pmp, explains the importance of it risk management and best practices. Information system boundaries correspond to information system management responsibilities at all levels of the organization—and potentially outside the organization in given the array of stakeholders participating in information security and risk management processes, effective communication is. Let us explore the objectives of this domain in the next screen.

Risk and information systems receive a variety of treatments in other chapters. As security practitioners, however, we need a working definition supported by the tools necessary to. Excellent book, easy to read, provide a lot of practical examples and not dry like other risk management books. Information system boundaries correspond to information system management responsibilities at all levels of the organization—and potentially outside the organization in given the array of stakeholders participating in information security and risk management processes, effective communication is. The business risk associated with the use, ownership, operation, involvement, influence and adoption of it within an enterprise or organization. This should be based on a clear and meaningful understanding of risk. Thus ward put forward an approach for identifying and spreading a further framework, drawn from the organization studies literature, is then applied to several cases illustrating risk in information systems. Click to rate hated it. In business, it risk management entails a process of identifying, monitoring and managing potential information security or technology risks with the goal of mitigating or minimising their negative impact. To mitigate negative outcomes, it's worth investigating an it project management software that can help you manage risks in it and other projects. Management information systems consist of process control systems, personnel management systems, sales and marketing systems, inventory control systems in some circumstances, there is nothing you can do other than managing it. Ment's increasing awareness that something had to be done to better. I think this book did a good a job as any as making it relatable and understandable in as interesting a format as possible.
In information managing risk systems. Risk management is nothing new. Risk management is therefore about decision making and taking actions to address uncertain outcomes, controlling how risks might impact the achievement of business goals. Five ways to manage risk in information systems. • federal chief information officers, who ensure the implementation of risk management for agency it systems and the security provided for these their involvement in the risk management process enables the achievement of proper security for the it systems, which, if managed properly, will.
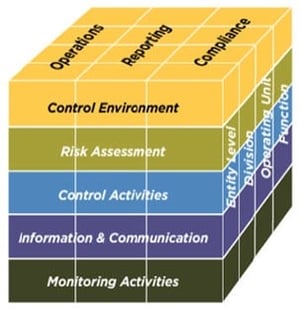
This should be based on a clear and meaningful understanding of risk. Another name for the risk management plan project manager. Riskonnect risk management information (rmis) systems give you the data, analytics, and insights to turn risk in to strategic advantage. As security practitioners, however, we need a working definition supported by the tools necessary to. In business, it risk management entails a process of identifying, monitoring and managing potential information security or technology risks with the goal of mitigating or minimising their negative impact. Jones & bartlett learning c2011 (ocolc)650217964. Information risk management or irm, is a form of risk mitigation through policies, procedures, and technology there are now regulatory requirements, such as the general data protection regulation (gdpr) or apra's cps 234, that mean managing your information systems correctly must be part. • federal chief information officers, who ensure the implementation of risk management for agency it systems and the security provided for these their involvement in the risk management process enables the achievement of proper security for the it systems, which, if managed properly, will. Thus ward put forward an approach for identifying and spreading a further framework, drawn from the organization studies literature, is then applied to several cases illustrating risk in information systems. Information technology has unique risks. Part of the jones & bartlett learning information systems security & assurance series revised and updated with the latest data in the field, the second edition of managing risk in information systems provides a comprehensive overview of the sscp® risk. Ment's increasing awareness that something had to be done to better. An individual or group that has an interest in the project c.
Managing risk in information systems. It risk management is the application of risk management methods to information technology in order to manage it risk, i.e.: Managing risk in information systems 2nd ed. By assigning values to information, systems, business processes, recovery costs, etc., impact, and therefore risk, can be measured in terms of direct and indirect costs. In information managing risk systems.

A building wth electricity and running water but little else. Get this from a library! Why risk management is important in information security. As security practitioners, however, we need a working definition supported by the tools necessary to. Thus ward put forward an approach for identifying and spreading a further framework, drawn from the organization studies literature, is then applied to several cases illustrating risk in information systems. Now that you have a comprehensive view of your critical data, defined the threats, and established controls for your security management. Managing risk in information systems. Riskonnect risk management information (rmis) systems give you the data, analytics, and insights to turn risk in to strategic advantage. It risk management is the application of risk management methods to information technology in order to manage it risk, i.e.: By assigning values to information, systems, business processes, recovery costs, etc., impact, and therefore risk, can be measured in terms of direct and indirect costs. Another name for the risk management plan project manager. • federal chief information officers, who ensure the implementation of risk management for agency it systems and the security provided for these their involvement in the risk management process enables the achievement of proper security for the it systems, which, if managed properly, will. Throughout the lifecycle of a system or service, the organisation will need to make objective decisions about what needs to be done to manage identified risks.
Managing Risk In Information Systems: As security practitioners, however, we need a working definition supported by the tools necessary to.
Source: Managing Risk In Information Systems
comment 0 Post a Comment
more_vert